Ever since the very beginning of the internet, there has been a type of malicious activity almost immune to technological progress in cyber-security, social engineering. Nowadays, the target of these practices can be anyone, including you and your coins.
The type of attacks known as phishing relies on the fallibility of human judgment and perception. Phishing, the most widespread form of attack, is used to extract sensitive data such as credit card numbers, social security numbers, passwords, and other confidential information from unaware users online by letting them submit this information directly to the attacker.
Trust your device
Your internet browser and software wallet are often prone to malware, viruses or various types of attacks. If you have the Trezor wallet, however, you are offline i.e. being isolated from the malicious attempts.
The fundamental purpose of safe hardware wallets such as Trezor or Ledger is to keep your recovery seed isolated. Nevertheless, you should always thoroughly check your device for confirmation of all features, especially when interacting with Trezor. Your PC should never require the use of your seed unless you want to recover the wallet (for example, after losing the device).
More, should you ever need to use the recovery seed to access your accounts, the device will always instruct you to enter the words in a shuffled order. We recommend entering the words of your seed directly on the hardware wallet instead of on PC. This will help you maximize the safety of your transactions.
Impersonation technique
The impersonation technique is one of the fastest to execute and technologically simplest to implement. The attacker usually impersonates a customer services agent or sales rep of the manufacturer of the wallet and tries to lure sensitive information from an unaware user using e-mails, phone communication or a spoofed website.
Remember, Trezor (SatoshiLabs) representatives will never ever ask for your recovery seed (in any form) or a credit card number.
If you ever have a problem with your device or would like to ask a question about Trezor-related issues, the only safe way of contacting Satoshi Labs is by sending a support ticket to their Support center. Alternatively, you can write your comments here on our website. We will do our best to answer all your questions.
SatoshiLabs do not provide phone call or live technical support. Therefore, never call numbers that claim to be associated with Trezor’s support team.
Many phishing techniques aim to bring you to a fraudulent site where all information can be collected and controlled by the attacker. Similarly to the impersonation techniques, these techniques are designed to rob you of your private keys.
DNS Spoofing (“DNS poisoning”)
is an attacking technique which takes advantage of the way DNS works to navigate the visitor in a wrong direction, making the site appear to be offline or even redirecting users to a server controlled by the attacker. On the other hand, BGP hijacking is a technique in which the hacker takes control of a group of IP prefixes assigned to a potential victim. Both methods can be identified by an invalid SSL certificate, however, users tend to overlook the warning, leading them to the malicious site. It is, therefore, crucial to carefully watch all signs, especially when working with sensitive things such as cryptocurrencies.
Unicode domain phishing
Another potential type of attack unicode domain phishing attack, also known as IDN homograph attack, relies on the fact that the affected browsers show Unicode characters used in domain names as standard characters, making them impossible to distinguish from domains that are legitimate.
While your browser may show the address as www.bitfinex.com the legitimate domain may be slightly different e.g. www.bítfínex.com.
If an attacker registers a domain that is visually indistinguishable from a legitimate one, he or she can trick users into trusting the site.
E-mail phishing
Another well-known technique is distributing SPAM e-mails aimed at luring from users name and password of any crypto exchange or their e-mail account/s.
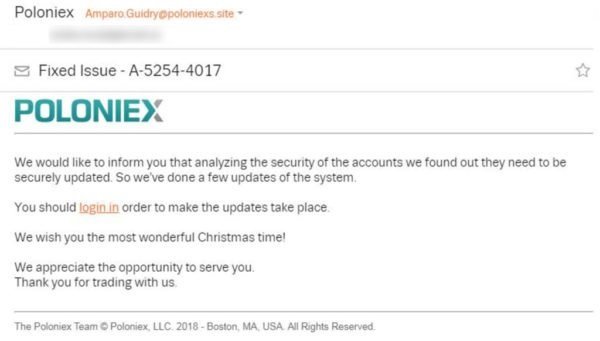
This is what a fraudulent e-mail may look like
The above screenshot depicts the photo of an e-mail which was sent to a crypto trader who then passed it onto Facebook as a means of warning for the rest of the users
Notice that the sender’s e-mail address is [email protected], while the official website of Poloniex is poloniex.com. (Notice that the end segment of the sender’s e-mail address should have been @poloniex.com!)
Cyber-squatting
Cyber-squatting or domain squatting refers to illegal domain name registration or use. While the forms differ, the goal remains the same: to steal or misspell a domain name. Cyber-squatting can also include “advertisers” who mimic domain names that are similar to famous, busy websites.
A few recommendations to protect yourself against becoming a victim of a phishing attack:
- Trust your device. Look for confirmation on the screen, especially when it involves transactions or your recovery seed
- Make sure the URL is exactly: https://wallet.trezor.ioor https://beta-wallet.trezor.io.
- Save the https://wallet.trezor.io as a bookmark to avoid misspelling it in the address bar of your browser
- Although the green lock on your browser (on the left-hand side from the address) may not be a guarantee of the authenticity of the website, be alarmed if it is missing
- Never give your recovery seed to anyone (including Trezor’s technical support, CEO or anyone else).
- Carefully observe the website addresses and watch out for any mistakes in the spelling or atypical characters.
- Use updated security software, install security patches and updates once available
- Avoid clicking on links in an e-mail or social media unless you are absolutely sure that these are authentic
- Pay close attention to shortened or incomplete links, especially on social media
- Remember, the representatives of SatoshiLabs (manufacturer of Trezor) or Ledger will never contact you on Facebook or by e-mail to give them any data